All Huawei FTTH modems ping qq.com , taobao.com and baidu.com every second . In a 24 hour cycle it generates approx 2 lac DNS queries
Its unnecessary load on my hardware and internet . I am using no branding , Elecroline firmware which is a generic Huawei HG8120XGA Ver - B ( XPON Voice Port + GE + FE
Due to this i have permanent 96% memory usage on this cheapo ONU
NextDNS free tier has monthly 3Lac DNS queries which are finished in 30 hours . Had to pickup Adguard DNS subscription which has 10 Million monthly quota so surviving but how to stop this ?
Why should BSNL allow this when Huawei is banned in India . Even if its unbranded hardware with generic firmware this should be stopped
How to kill this ?
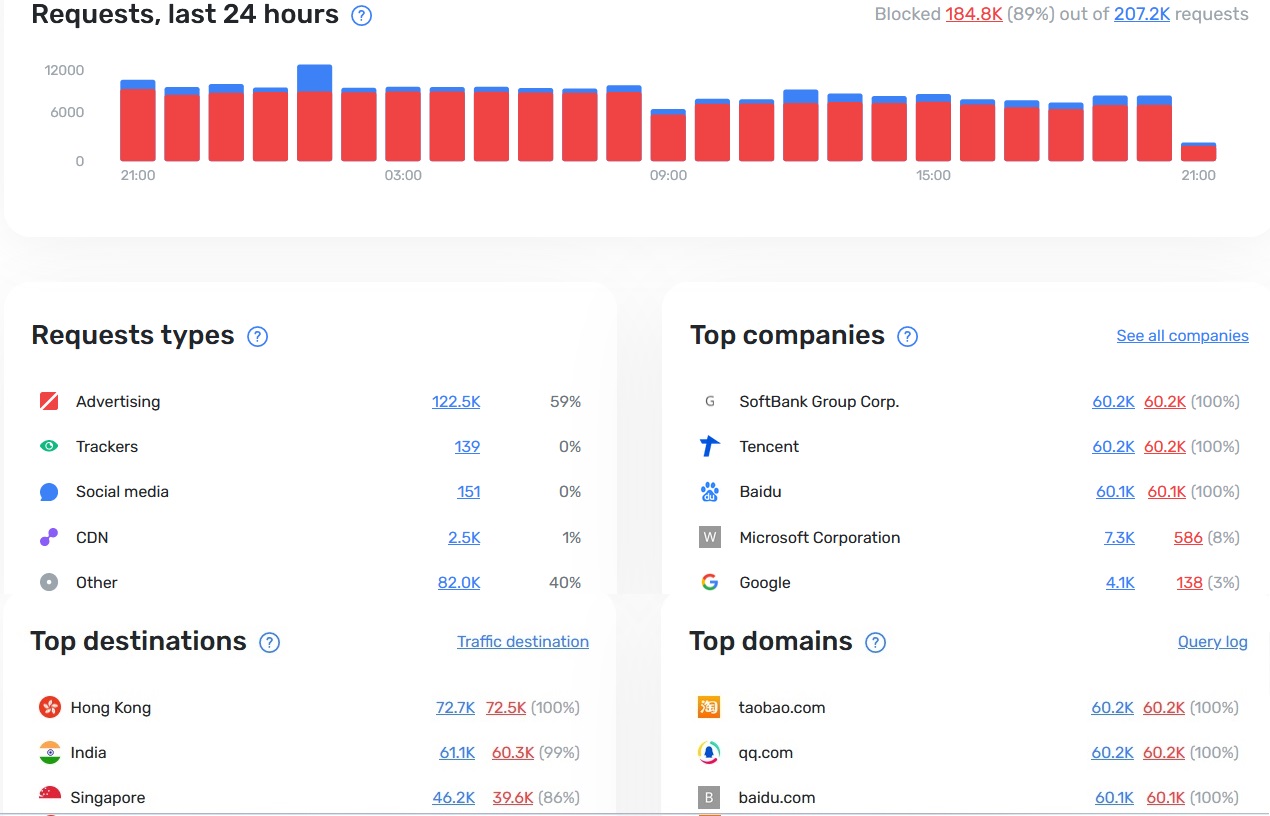
Its unnecessary load on my hardware and internet . I am using no branding , Elecroline firmware which is a generic Huawei HG8120XGA Ver - B ( XPON Voice Port + GE + FE
Due to this i have permanent 96% memory usage on this cheapo ONU
NextDNS free tier has monthly 3Lac DNS queries which are finished in 30 hours . Had to pickup Adguard DNS subscription which has 10 Million monthly quota so surviving but how to stop this ?
Why should BSNL allow this when Huawei is banned in India . Even if its unbranded hardware with generic firmware this should be stopped
How to kill this ?

