Do ur Standalone Root CA and Standalone Subordinate CA needs to be online in order to confirm Trust Root Path for our users ....
Mine testing Setup ... Main Goal > AutoEnrollment for End Users
Standalone Root CA > Standalone Subordinate CA > Enterprise Subordinate Issuing CA > End Users ...
CA Servers and End Users are on same Network Segments
CA Servers : 10.x.x.x.
End Users : 10.x.x.x
As mentioned i had setup all the systems , and tried autoenrollment With 2k3 Sp2 PKI and Win Xp Sp2 Clients ...
The interca and rootca ( both standalone ) are offline ...
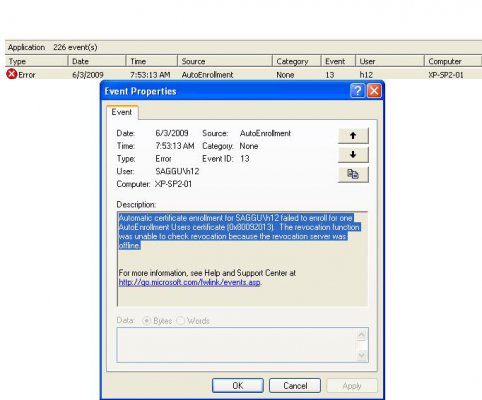
When a client system tried to autoenroll,d for the first time ... it does,nt got autoenrolled ...
Wireshark trace depicts that the client ( xp_sp2_01 ) was looking for interca ( which is offline ) ... why is it looking for Interca system ( doing NBNS broadcasts ... and suppose if our INTERCA is on completely different Network Negment where it can,t be reached via a NBNS name broadcast ... how would clients know abt Interca ... [ leaving the clients LMHOSTS as a valid option ] ... )
Wireshark trace has be attached ...
If our InterCA is online ( rootca is still offline ) , everything works fine ...
Now do our Standalone InterCA needs to online forever to complete AutoEnrollment for our clients ... or any other way to handle this out ...
:huh:
Mine testing Setup ... Main Goal > AutoEnrollment for End Users
Standalone Root CA > Standalone Subordinate CA > Enterprise Subordinate Issuing CA > End Users ...
CA Servers and End Users are on same Network Segments
CA Servers : 10.x.x.x.
End Users : 10.x.x.x
As mentioned i had setup all the systems , and tried autoenrollment With 2k3 Sp2 PKI and Win Xp Sp2 Clients ...
The interca and rootca ( both standalone ) are offline ...
When a client system tried to autoenroll,d for the first time ... it does,nt got autoenrolled ...
Wireshark trace depicts that the client ( xp_sp2_01 ) was looking for interca ( which is offline ) ... why is it looking for Interca system ( doing NBNS broadcasts ... and suppose if our INTERCA is on completely different Network Negment where it can,t be reached via a NBNS name broadcast ... how would clients know abt Interca ... [ leaving the clients LMHOSTS as a valid option ] ... )
Wireshark trace has be attached ...
If our InterCA is online ( rootca is still offline ) , everything works fine ...
Now do our Standalone InterCA needs to online forever to complete AutoEnrollment for our clients ... or any other way to handle this out ...
:huh: