enthusiast29
Juggernaut
Hi, I need a little help from networking experts here...
I have the following setup at my home:
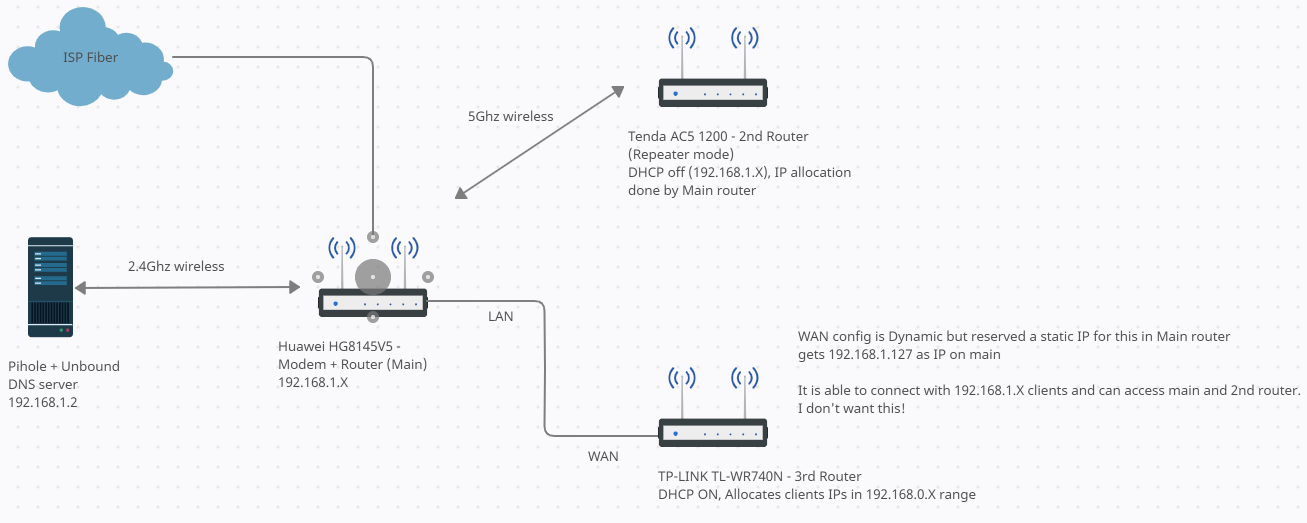
I have set up same IP range for both current routers (ISP provided and 2nd router):
192.168.1.x
DHCP allocation on 2nd router is OFF and is handled by the main router itself. So all devices on both routers exist on same network and can talk to each other.
main router clients - office equipment, VOIP, LAN/WLAN connections, basically things I own
Router 2 clients - other family devices connected via WLAN
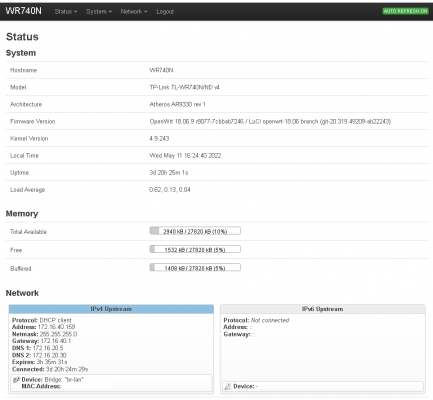
The above network has a self hosted DNS server solution using pihole + unbound running on static IP 192.168.1.2.
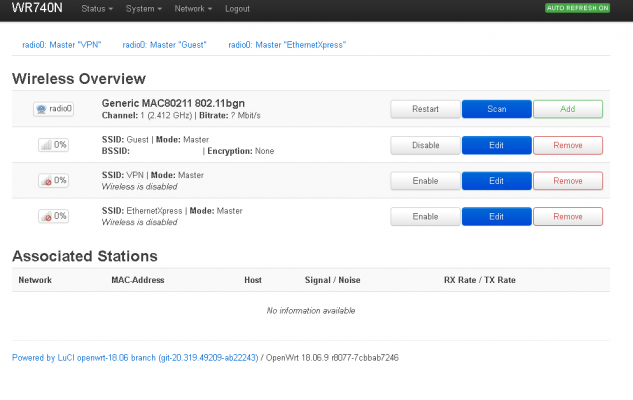
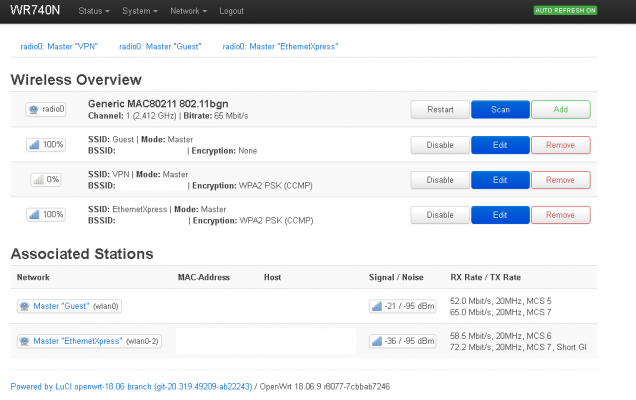
3rd router (connected directly with main through LAN) would be for guests with complete isolation from all other networks and bypassing pihole + unbound solution and instead using Cloudflare DNS. I also need this in case of emergencies and troubleshooting as well if something is blocked on pihole and I don't have time to figure out but need a temporary solution to check.
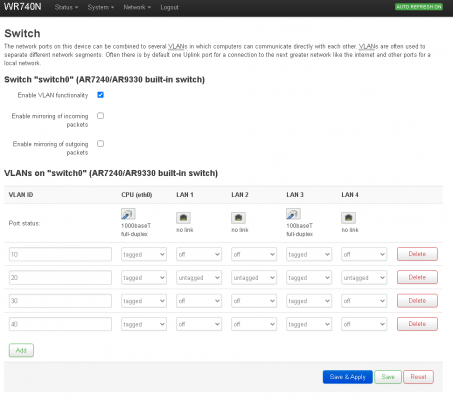
My plan is to use 192.168.0.x range on this 3rd router and enable DHCP allocation on that router itself which should according to my understanding isolate the clients on this router from the main/2nd router.
My problem:
I am able to set this up easily and 3rd router works and all my clients on 3rd router get assigned an IP in 192.168.0.x range but still can access and talk with all devices of 192.168.1.x range but vice-versa is not true, i.e., I cannot access 192.168.0.x range using the main router or 2nd router (192.168.1.x range) not that I need to (better that I can't) but why the reverse is possible? In any case I don't want guest network to be able to access the main.
What's happening...
-------------------------------------------------------
Main can access 2nd (both 192.168.1.x subnet) <-- intended
2nd can access Main (both 192.168.1.x subnet) <-- intended
3rd can access Main and 2nd (even when 3rd is on 192.168.0.x subnet) <-- not intended, I don't want this!
Main and 2nd cannot access 3rd (which is fine) <-- intended
-------------------------------------------------------
I am unable to figure out how to isolate the 192.168.0.x network on the 3rd router. Can anyone help me with this?
I have the following setup at my home:
I have set up same IP range for both current routers (ISP provided and 2nd router):
192.168.1.x
DHCP allocation on 2nd router is OFF and is handled by the main router itself. So all devices on both routers exist on same network and can talk to each other.
main router clients - office equipment, VOIP, LAN/WLAN connections, basically things I own
Router 2 clients - other family devices connected via WLAN
The above network has a self hosted DNS server solution using pihole + unbound running on static IP 192.168.1.2.
3rd router (connected directly with main through LAN) would be for guests with complete isolation from all other networks and bypassing pihole + unbound solution and instead using Cloudflare DNS. I also need this in case of emergencies and troubleshooting as well if something is blocked on pihole and I don't have time to figure out but need a temporary solution to check.
My plan is to use 192.168.0.x range on this 3rd router and enable DHCP allocation on that router itself which should according to my understanding isolate the clients on this router from the main/2nd router.
My problem:
I am able to set this up easily and 3rd router works and all my clients on 3rd router get assigned an IP in 192.168.0.x range but still can access and talk with all devices of 192.168.1.x range but vice-versa is not true, i.e., I cannot access 192.168.0.x range using the main router or 2nd router (192.168.1.x range) not that I need to (better that I can't) but why the reverse is possible? In any case I don't want guest network to be able to access the main.
What's happening...
-------------------------------------------------------
Main can access 2nd (both 192.168.1.x subnet) <-- intended
2nd can access Main (both 192.168.1.x subnet) <-- intended
3rd can access Main and 2nd (even when 3rd is on 192.168.0.x subnet) <-- not intended, I don't want this!
Main and 2nd cannot access 3rd (which is fine) <-- intended
-------------------------------------------------------
I am unable to figure out how to isolate the 192.168.0.x network on the 3rd router. Can anyone help me with this?
Last edited: