savrom
Disciple
This week in Ransomware
Article Source: bleepingcomputer.com
The Week in Ransomware - January 20th 2017 - Satan RaaS, Spora, Locky, and More
This week we continue to see more ransomware being released as well as changes in the distribution of the larger ransomware infections. For example, Locky has had a very low distribution lately since the holidays, but according to the Cisco Talos Group, it is starting to pick up again. We also seeing the Spora ransomware being thrown into the mix, where malware distribution sites that typically were pushing Cerber, started to push Locky and Spora.
Another big story is the discovery of a new Ransomware as a Service called Satan. RaaS is nothing new, but what makes Satan stand out is the RaaS developer actually offering help in creating malicious documents and macros that can be used to distribute their ransomware.
The good news is that Fabian Wosar of Emsisoft was able to decrypt two more ransomware variants this week, so victims who are affected by them will be able to get their files back for free.
Contributors and those who provided new ransomware information and stories this week include: @malwrhunterteam, @DanielGallagher, @demonslay335, @PolarToffee, @fwosar, @campuscodi, @BleepinComputer, @struppigel, @JAMESWT_MHT, @Seifreed, @nyxbone, @0xDUDE, @nmerrigan, @jiriatvirlab, @malware_traffic, @GossiTheDog, @MalwareTechBlog, @CheckPointSW, @avast_antivirus, @Racco42, @Fortinet, @Xylit0l, @JakubKroustek, @TalosSecurity, @jaesonschultz, @infosec_nick.
If you are interested in ransomware or InfoSec, I suggest you follow all of them on Twitter.
January 13th 2017
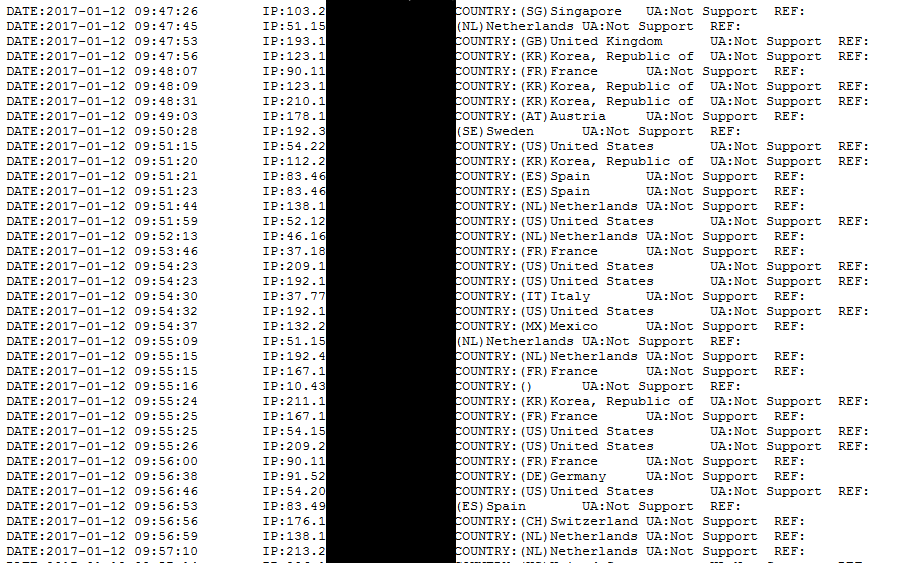
Misconfigured Server Gives Insight Into Cerber Ransomware Operation
A security researched named Racco42 discovered a vulnerability on Thursday, January 12th that allowed researchers to gain access to one of the servers used by the Cerber gang, which can be used to extract basic statistics about their operation.
January 14th 2017
New SamSam/Samas Ransomware Variant Discovered
Michael Gillespie has discovered a new SamSam/Samas ransomware that uses the extension .powerfulldecrypt and a ransom note named WE-MUST-DEC-FILES.html.
![C2Jj0K4XAAAcq2E[1].jpg](/proxy.php?image=https%3A%2F%2Fwww.bleepstatic.com%2Fimages%2Fnews%2Fcolumns%2Fweek-in-ransomware%2F1-20-17%2FC2Jj0K4XAAAcq2E%5B1%5D.jpg&hash=e8873e2ca2f9552058237081e43b4196)
January 15th 2017
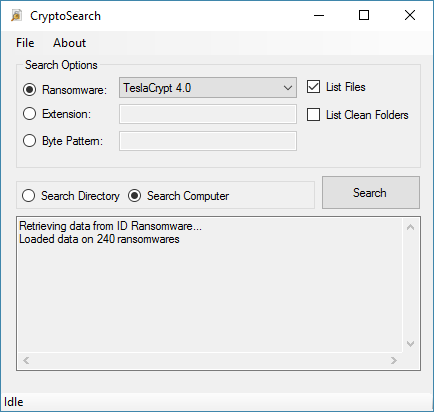
CryptoSearch Finds Files Encrypted by Ransomware, Moves Them to New Location
Security researcher Michael Gillespie has developed a new Windows app to help victims of ransomware infections.
Named CryptoSearch, this tool identifies files encrypted by several types of ransomware families and provides the user with the option to copy or move the files to a new location, in hopes that a decrypter that can recover the locked files will be released in the future.
January 17th 2017
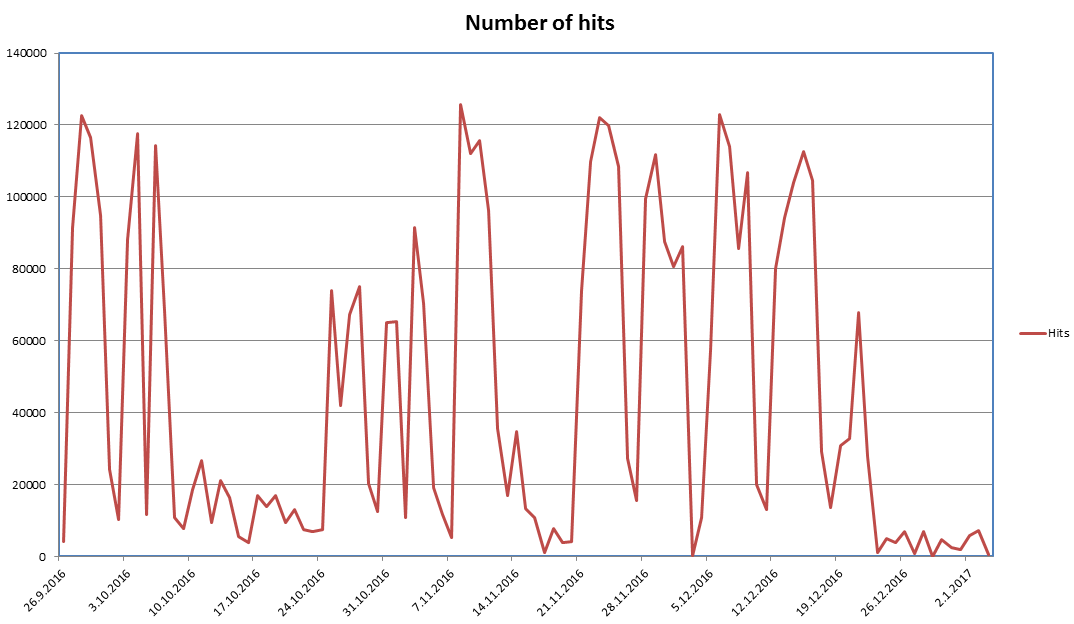
Locky Ransomware Activity Goes Down by 81%
Security firms Avast and Check Point, and security researchers Kevin Beaumont, MalwareTech, and MalwareHunterTeam have noticed that for more than four weeks, the only source of Locky ransomware infections has been through spam campaigns that distributed the Kovter click-fraud malware, as the primary source of Locky infections, the Necurs botnet, has been offline for the Christmas and New Year holidays.
Minor changes to Cerber Discovered
MalwareHunterTeam discovered that Cerber changed the ransom note names to _HELP_HELP_HELP_%random%.hta & _HELP_HELP_HELP_%random%.jpg. It uses the IP ranges 90.2..1.0/27, 90.3.1.0/27, 91.239.24.0/23 for UDP statistics.
Previous Cerber Distribution Sites start Distributing Spora
MalwareHunterTeam notes that the "malware center" which was used to spread Cerber exclusively in past month(s?), is now spreading Spora. Brad Duncan also notices distribution campaigns switching from Cerber to Locky and Spora.
January 18th 2017
Indiana Cancer Agency Hit by Aggressive Ransomware Group
A ransomware group has infected the computers of an Indiana-based cancer agency and have asked for a large payment of 50 Bitcoin ($44,800). The victim is Cancer Services of East Central Indiana-Little Red Door, an organization that helps "reduce the financial and emotional burdens of those dealing with a cancer diagnosis."
New SamSam/Samas Variant Discovered
Michael Gillespie has discovered a new SamSam/Samas ransomware that uses the extension .noproblemwedecfilesand a ransom note named 000-No-PROBLEM-WE-DEC-FILES.html.
Database Ransom Attacks Hit CouchDB and Hadoop Servers
For the past week, unknown groups of cyber-criminals have taken control of and wiped data from CouchDB and Hadoop databases, in some cases asking for a ransom fee to return the stolen files, but in some cases, destroying data just for fun.
These incidents come after crooks hijacked and held data ransom from MongoDB databases since the start of the year.
Spora - the Shortcut Worm that is also a Ransomware
GData malware analyst Karsten Hahn discusses how Spora spreads via USB drives like Gamarue and Dinihou aka Jenxcus whilst also encrypting files.
Merry X-Mas Decryptor Updated
Fabian Wosar of Emsisoft has updated their Merry X-Mas decryptor to now support the variant that uses the .MERRY extension for encrypted files.
Without Necurs, Locky Struggles
Cisco Talos Group researchers Nick Biasini and Jaeson Schultz wrote an article about how "Locky has been a devastating force for the last year in the spam and ransomware landscape. The Locky variant of ransomware has been responsible for huge amounts of spam messages being sent on a daily basis. The main driver behind this traffic is the Necurs botnet. This botnet is responsible for the majority of Locky and Dridex activity. Periodically Necurs goes offline and during these periods we typically see Locky activity decrease drastically. One of these periods is currently ongoing."
New Brazilian Ransomware Discovered
Jakub Kroustek discovered a new Brazilian ransomware that appends .id-%ID%_garryweber@protonmail.ch to encrypted files and creates ransom notes named HOW_OPEN_FILES.html.
![C2e1sEjWIAAo7kV[1].jpg](/proxy.php?image=https%3A%2F%2Fwww.bleepstatic.com%2Fimages%2Fnews%2Fcolumns%2Fweek-in-ransomware%2F1-20-17%2FC2e1sEjWIAAo7kV%5B1%5D.jpg&hash=ce739651f74dc97070b422bb50345c5a)
January 19th 2017
Cerber Changes Ransom Note Filenames
xXToffeeXx noticed that Cerber has switched the ransom note names to _HOW_TO_DECRYPT_[A-Z0-9]{4-8}_.jpg and .hta notes since about the 14th.
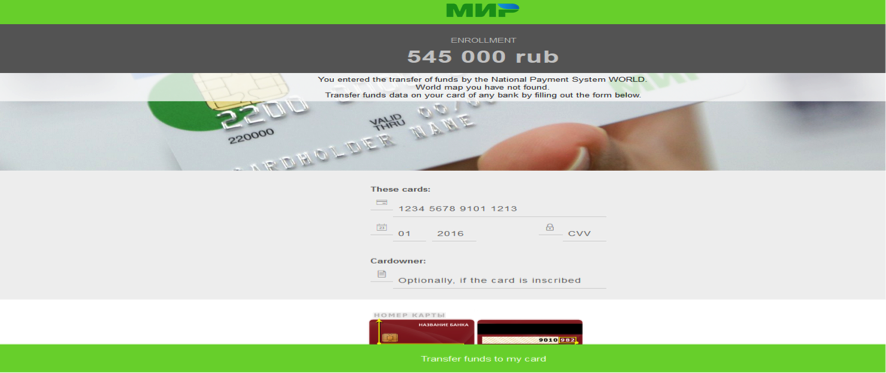
Android Ransomware Locks Phone and Asks for Credit Card Number
A new ransomware family is targeting Android devices, locking access to the screen, and constantly pestering the user to enter his payment card details. According to Fortinet researcher Kai Lu, the one who discovered this new threat, the ransomware appears to be targeting only Russian-speaking users, as its ransom note is only available in Russian. A translated version of the ransom note is available below.
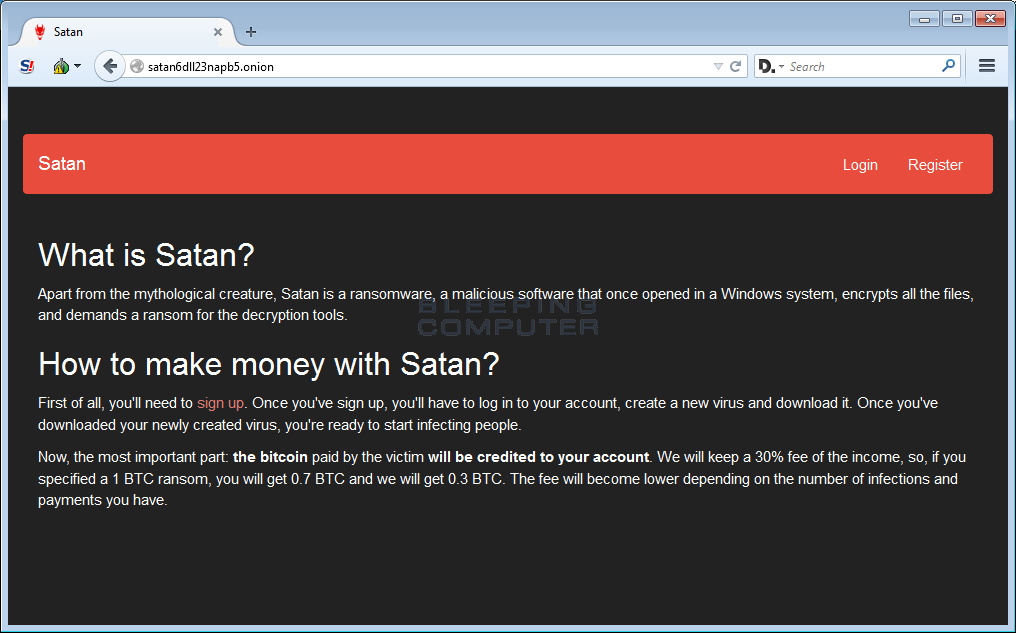
New Satan Ransomware available through a Ransomware as a Service.
A new Ransomware as a Service, or RaaS, called Satan has been discovered by security researcher Xylitol. This service allows any wannabe criminal to register an account and create their very own customized version of the Satan Ransomware. The Satan Ransomware will encrypt data and append the .stn extension to encrypted files. It will also display a ransom note named HELP_DECRYPT_FILES.html.
New Turkish In-Development Ransomware Discovered
Karsten Hahn has discovered a new in-development Turkish ransomware that intends to append the .sifreli extension to encrypted files. Doesn't appear to be doing much now.
![C2hM_LdXAAAou8E[1].jpg](/proxy.php?image=https%3A%2F%2Fwww.bleepstatic.com%2Fimages%2Fnews%2Fcolumns%2Fweek-in-ransomware%2F1-20-17%2FC2hM_LdXAAAou8E%5B1%5D.jpg&hash=b4715c4c2c9f676bf32165e8238a6f3d)
New In-development Hidden Tear Ransomware called CryptoShadow
Karsten Hahn has discovered a new in-development HiddenTear ransomware called CryptoShadow that appends the .doomed extension to encrypted files and creates a ransom note named LEER_INMEDIATAMENTE.txt.
January 20th 2017
Ransomware Locks Down Public Libraries at All Locations Across Saint Louis
The Saint Louis Public Library (SLPL) announced that ransomware had hit all computers at all their branches across the city forcing the institution to halt all operations for the time being. Over 700 computers at all of SLPL's 16 branches have been hit. According to library spokesperson Jen Hatton, SLPL doesn't intend to pay the ransom, which is around $35,000, about $50 per infected PC.
Decryptor for the Globe Imposter Released
Fabian Wosar of Emsisoft haas released a decryptor for a Globe ransomware imposter. This ransomware will append the *.crypt extension to encrypted files and create ransom notes named HOW_OPEN_FILES.hta.
New DNRansomware Discovered
I found a new ransomware from our friend humanpuff69 called DNRansomware. This ransomware will encrypt data using a static key and append the .****ed extension to encrypted files. It will then show you a lock screen. If you enter the code 83KYG9NW-3K39V-2T3HJ-93F3Q-GT into the lock screen, it will automatically decrypt your files for you.
![C2obaq8XUAAkGXK[1].jpg](/proxy.php?image=https%3A%2F%2Fwww.bleepstatic.com%2Fimages%2Fnews%2Fcolumns%2Fweek-in-ransomware%2F1-20-17%2FC2obaq8XUAAkGXK%5B1%5D.jpg&hash=20a6825d63b5b03f89bca4fe0c28c028)
New Variant of the Jhon Woddy Ransomware Discovered
I found a new Jhon Woddy Ransomware variant that is the same codebase as DNRansomware. This ransomware will append the .killedXXX. extension to encrypted files. The lock screen password is M3VZ>5BwGGVH, and once you enter the password the program is supposed to decrypt your files automatically. Unfortunately, this routine is broken so you should use Michael Gillespie's decryptor instead. The password to the decryptor's zip file is false-positive.
According to Jiri Kropac, the source code for this ransomware is floating around so we will most likely see more variants released in the future.
![C2ojnrDW8AAONyx[1].jpg](/proxy.php?image=https%3A%2F%2Fwww.bleepstatic.com%2Fimages%2Fnews%2Fcolumns%2Fweek-in-ransomware%2F1-20-17%2FC2ojnrDW8AAONyx%5B1%5D.jpg&hash=71cbd66533a6a4ba7575debe70cef774)
Article Source: bleepingcomputer.com
The Week in Ransomware - January 20th 2017 - Satan RaaS, Spora, Locky, and More
This week we continue to see more ransomware being released as well as changes in the distribution of the larger ransomware infections. For example, Locky has had a very low distribution lately since the holidays, but according to the Cisco Talos Group, it is starting to pick up again. We also seeing the Spora ransomware being thrown into the mix, where malware distribution sites that typically were pushing Cerber, started to push Locky and Spora.
Another big story is the discovery of a new Ransomware as a Service called Satan. RaaS is nothing new, but what makes Satan stand out is the RaaS developer actually offering help in creating malicious documents and macros that can be used to distribute their ransomware.
The good news is that Fabian Wosar of Emsisoft was able to decrypt two more ransomware variants this week, so victims who are affected by them will be able to get their files back for free.
Contributors and those who provided new ransomware information and stories this week include: @malwrhunterteam, @DanielGallagher, @demonslay335, @PolarToffee, @fwosar, @campuscodi, @BleepinComputer, @struppigel, @JAMESWT_MHT, @Seifreed, @nyxbone, @0xDUDE, @nmerrigan, @jiriatvirlab, @malware_traffic, @GossiTheDog, @MalwareTechBlog, @CheckPointSW, @avast_antivirus, @Racco42, @Fortinet, @Xylit0l, @JakubKroustek, @TalosSecurity, @jaesonschultz, @infosec_nick.
If you are interested in ransomware or InfoSec, I suggest you follow all of them on Twitter.
January 13th 2017
Misconfigured Server Gives Insight Into Cerber Ransomware Operation
A security researched named Racco42 discovered a vulnerability on Thursday, January 12th that allowed researchers to gain access to one of the servers used by the Cerber gang, which can be used to extract basic statistics about their operation.

January 14th 2017
New SamSam/Samas Ransomware Variant Discovered
Michael Gillespie has discovered a new SamSam/Samas ransomware that uses the extension .powerfulldecrypt and a ransom note named WE-MUST-DEC-FILES.html.
![C2Jj0K4XAAAcq2E[1].jpg](/proxy.php?image=https%3A%2F%2Fwww.bleepstatic.com%2Fimages%2Fnews%2Fcolumns%2Fweek-in-ransomware%2F1-20-17%2FC2Jj0K4XAAAcq2E%5B1%5D.jpg&hash=e8873e2ca2f9552058237081e43b4196)
January 15th 2017
CryptoSearch Finds Files Encrypted by Ransomware, Moves Them to New Location
Security researcher Michael Gillespie has developed a new Windows app to help victims of ransomware infections.
Named CryptoSearch, this tool identifies files encrypted by several types of ransomware families and provides the user with the option to copy or move the files to a new location, in hopes that a decrypter that can recover the locked files will be released in the future.

January 17th 2017
Locky Ransomware Activity Goes Down by 81%
Security firms Avast and Check Point, and security researchers Kevin Beaumont, MalwareTech, and MalwareHunterTeam have noticed that for more than four weeks, the only source of Locky ransomware infections has been through spam campaigns that distributed the Kovter click-fraud malware, as the primary source of Locky infections, the Necurs botnet, has been offline for the Christmas and New Year holidays.

Minor changes to Cerber Discovered
MalwareHunterTeam discovered that Cerber changed the ransom note names to _HELP_HELP_HELP_%random%.hta & _HELP_HELP_HELP_%random%.jpg. It uses the IP ranges 90.2..1.0/27, 90.3.1.0/27, 91.239.24.0/23 for UDP statistics.
Previous Cerber Distribution Sites start Distributing Spora
MalwareHunterTeam notes that the "malware center" which was used to spread Cerber exclusively in past month(s?), is now spreading Spora. Brad Duncan also notices distribution campaigns switching from Cerber to Locky and Spora.
January 18th 2017
Indiana Cancer Agency Hit by Aggressive Ransomware Group
A ransomware group has infected the computers of an Indiana-based cancer agency and have asked for a large payment of 50 Bitcoin ($44,800). The victim is Cancer Services of East Central Indiana-Little Red Door, an organization that helps "reduce the financial and emotional burdens of those dealing with a cancer diagnosis."
New SamSam/Samas Variant Discovered
Michael Gillespie has discovered a new SamSam/Samas ransomware that uses the extension .noproblemwedecfilesand a ransom note named 000-No-PROBLEM-WE-DEC-FILES.html.
Database Ransom Attacks Hit CouchDB and Hadoop Servers
For the past week, unknown groups of cyber-criminals have taken control of and wiped data from CouchDB and Hadoop databases, in some cases asking for a ransom fee to return the stolen files, but in some cases, destroying data just for fun.
These incidents come after crooks hijacked and held data ransom from MongoDB databases since the start of the year.
Spora - the Shortcut Worm that is also a Ransomware
GData malware analyst Karsten Hahn discusses how Spora spreads via USB drives like Gamarue and Dinihou aka Jenxcus whilst also encrypting files.
Merry X-Mas Decryptor Updated
Fabian Wosar of Emsisoft has updated their Merry X-Mas decryptor to now support the variant that uses the .MERRY extension for encrypted files.
Without Necurs, Locky Struggles
Cisco Talos Group researchers Nick Biasini and Jaeson Schultz wrote an article about how "Locky has been a devastating force for the last year in the spam and ransomware landscape. The Locky variant of ransomware has been responsible for huge amounts of spam messages being sent on a daily basis. The main driver behind this traffic is the Necurs botnet. This botnet is responsible for the majority of Locky and Dridex activity. Periodically Necurs goes offline and during these periods we typically see Locky activity decrease drastically. One of these periods is currently ongoing."
New Brazilian Ransomware Discovered
Jakub Kroustek discovered a new Brazilian ransomware that appends .id-%ID%_garryweber@protonmail.ch to encrypted files and creates ransom notes named HOW_OPEN_FILES.html.
![C2e1sEjWIAAo7kV[1].jpg](/proxy.php?image=https%3A%2F%2Fwww.bleepstatic.com%2Fimages%2Fnews%2Fcolumns%2Fweek-in-ransomware%2F1-20-17%2FC2e1sEjWIAAo7kV%5B1%5D.jpg&hash=ce739651f74dc97070b422bb50345c5a)
January 19th 2017
Cerber Changes Ransom Note Filenames
xXToffeeXx noticed that Cerber has switched the ransom note names to _HOW_TO_DECRYPT_[A-Z0-9]{4-8}_.jpg and .hta notes since about the 14th.
Android Ransomware Locks Phone and Asks for Credit Card Number
A new ransomware family is targeting Android devices, locking access to the screen, and constantly pestering the user to enter his payment card details. According to Fortinet researcher Kai Lu, the one who discovered this new threat, the ransomware appears to be targeting only Russian-speaking users, as its ransom note is only available in Russian. A translated version of the ransom note is available below.

New Satan Ransomware available through a Ransomware as a Service.
A new Ransomware as a Service, or RaaS, called Satan has been discovered by security researcher Xylitol. This service allows any wannabe criminal to register an account and create their very own customized version of the Satan Ransomware. The Satan Ransomware will encrypt data and append the .stn extension to encrypted files. It will also display a ransom note named HELP_DECRYPT_FILES.html.

New Turkish In-Development Ransomware Discovered
Karsten Hahn has discovered a new in-development Turkish ransomware that intends to append the .sifreli extension to encrypted files. Doesn't appear to be doing much now.
![C2hM_LdXAAAou8E[1].jpg](/proxy.php?image=https%3A%2F%2Fwww.bleepstatic.com%2Fimages%2Fnews%2Fcolumns%2Fweek-in-ransomware%2F1-20-17%2FC2hM_LdXAAAou8E%5B1%5D.jpg&hash=b4715c4c2c9f676bf32165e8238a6f3d)
New In-development Hidden Tear Ransomware called CryptoShadow
Karsten Hahn has discovered a new in-development HiddenTear ransomware called CryptoShadow that appends the .doomed extension to encrypted files and creates a ransom note named LEER_INMEDIATAMENTE.txt.
January 20th 2017
Ransomware Locks Down Public Libraries at All Locations Across Saint Louis
The Saint Louis Public Library (SLPL) announced that ransomware had hit all computers at all their branches across the city forcing the institution to halt all operations for the time being. Over 700 computers at all of SLPL's 16 branches have been hit. According to library spokesperson Jen Hatton, SLPL doesn't intend to pay the ransom, which is around $35,000, about $50 per infected PC.
Decryptor for the Globe Imposter Released
Fabian Wosar of Emsisoft haas released a decryptor for a Globe ransomware imposter. This ransomware will append the *.crypt extension to encrypted files and create ransom notes named HOW_OPEN_FILES.hta.
New DNRansomware Discovered
I found a new ransomware from our friend humanpuff69 called DNRansomware. This ransomware will encrypt data using a static key and append the .****ed extension to encrypted files. It will then show you a lock screen. If you enter the code 83KYG9NW-3K39V-2T3HJ-93F3Q-GT into the lock screen, it will automatically decrypt your files for you.
![C2obaq8XUAAkGXK[1].jpg](/proxy.php?image=https%3A%2F%2Fwww.bleepstatic.com%2Fimages%2Fnews%2Fcolumns%2Fweek-in-ransomware%2F1-20-17%2FC2obaq8XUAAkGXK%5B1%5D.jpg&hash=20a6825d63b5b03f89bca4fe0c28c028)
New Variant of the Jhon Woddy Ransomware Discovered
I found a new Jhon Woddy Ransomware variant that is the same codebase as DNRansomware. This ransomware will append the .killedXXX. extension to encrypted files. The lock screen password is M3VZ>5BwGGVH, and once you enter the password the program is supposed to decrypt your files automatically. Unfortunately, this routine is broken so you should use Michael Gillespie's decryptor instead. The password to the decryptor's zip file is false-positive.
According to Jiri Kropac, the source code for this ransomware is floating around so we will most likely see more variants released in the future.
![C2ojnrDW8AAONyx[1].jpg](/proxy.php?image=https%3A%2F%2Fwww.bleepstatic.com%2Fimages%2Fnews%2Fcolumns%2Fweek-in-ransomware%2F1-20-17%2FC2ojnrDW8AAONyx%5B1%5D.jpg&hash=71cbd66533a6a4ba7575debe70cef774)

