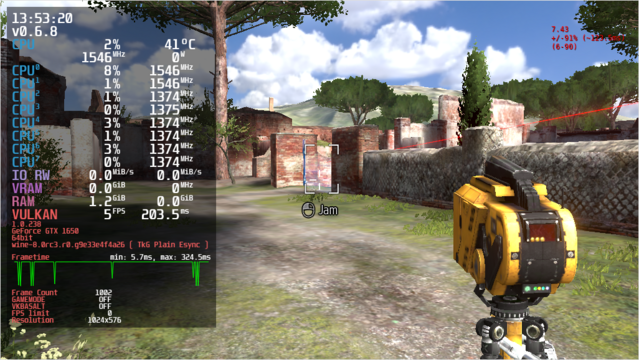
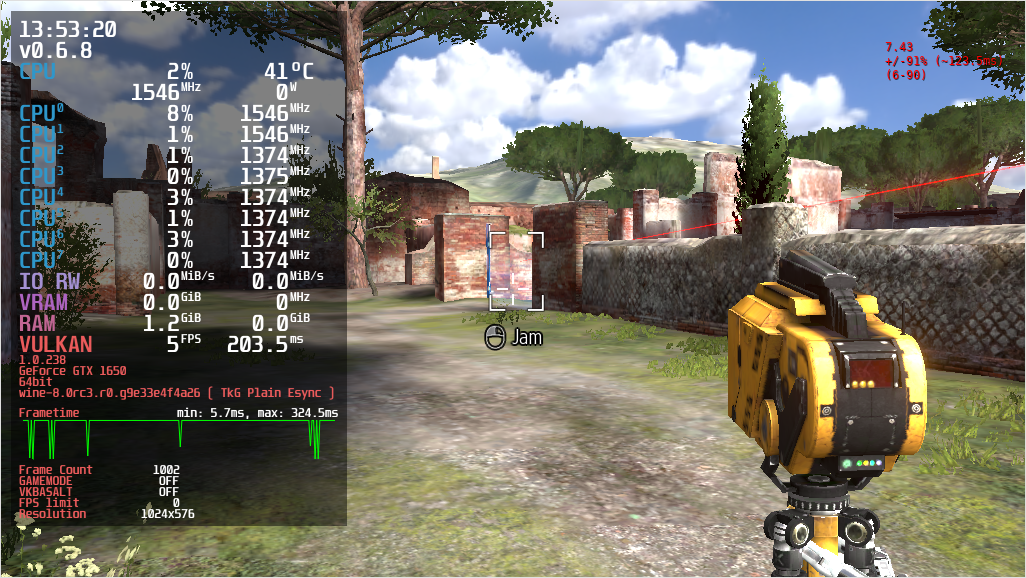
The Wine team is proud to announce that the stable release Wine 8.0
is now available.
What's new in Wine 8.0
======================
*** PE modules
- After 4 years of work, the PE conversion is finally complete: all modules can
be built in PE format. This is an important milestone on the road to supporting
various features such as copy protection, 32-bit applications on 64-bit hosts,
Windows debuggers, x86 applications on ARM, etc.
However, some modules still perform direct calls between the PE and the Unix
part, instead of going through the NT system call interface. The remaining
direct calls will be removed during the Wine 8.x development phase.
- A special syscall dispatcher is used for PE -> Unix transitions, to avoid the
overhead of a full NT system call. This minimizes the performance impact of the
new architecture, in particular for the OpenGL and Vulkan libraries.
- Building mixed Windows/Unix libraries in ELF format (.dll.so libraries) is
still supported for use in Winelib applications. However, such applications
won't support features enabled by the NT syscall interface, such as WoW64
without 32-bit libraries.
*** WoW64
- WoW64 thunks are implemented for essentially all Unix libraries, enabling a
32-bit PE module to call a 64-bit Unix library. Once the remaining direct
PE/Unix calls have been removed, this will make it fully possible to run
32-bit Windows applications without any 32-bit Unix library.
- When the 32-bit Wine loader isn't found, 32-bit applications are started in
the new experimental "Windows-like" WoW64 mode (where 32-bit code runs inside
a 64-bit host process). This mode can be enabled by building with the
'--enable-archs' configure option. This is still under development and not yet
recommended for general use. Since in case of configuration errors it is
possible for it to be triggered inadvertently, applications started in this
mode print the warning "starting in experimental wow64 mode".
 chaos.social
chaos.social