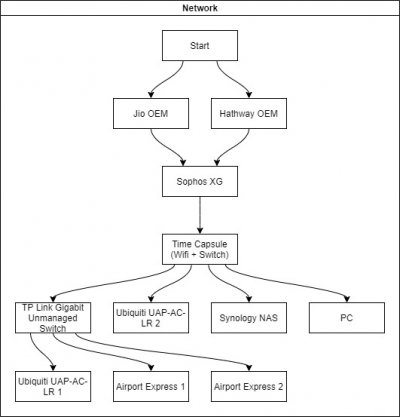
My home network is little dated and its time to update it.
Security is the primary focus, looking for absolute control over the devices in network, should be able to define which client can access internet and what not.
Planing to build something which could last a decade.
my current setup looks something like:
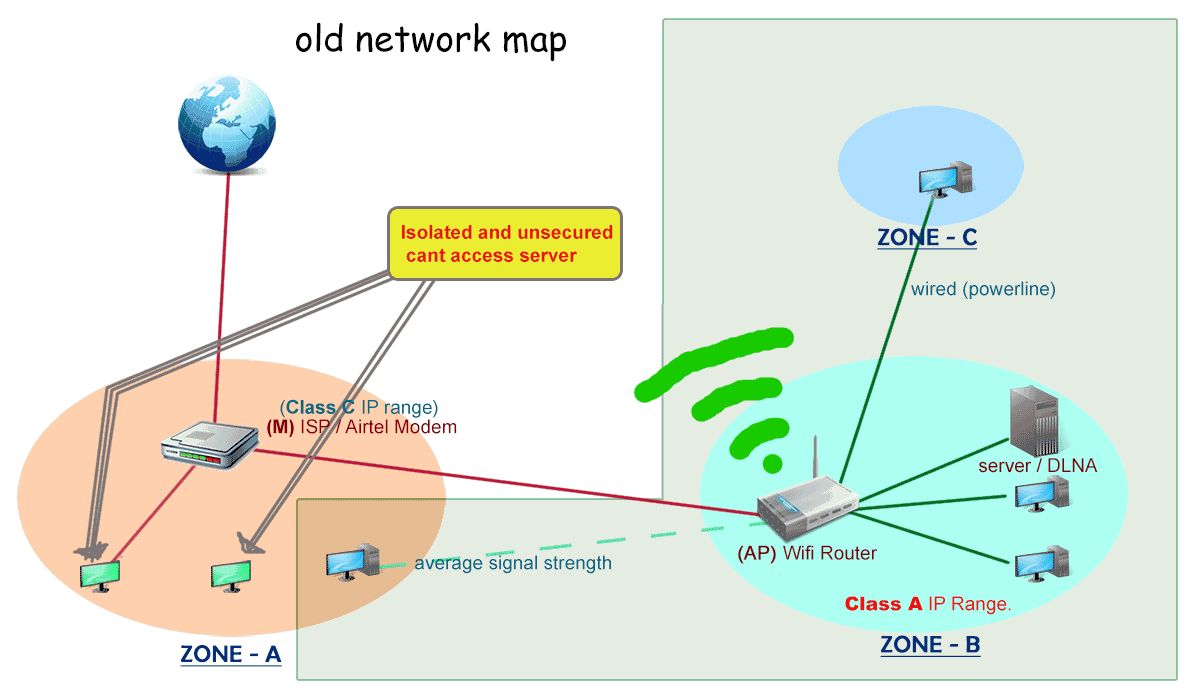
With time, new clients added in network and few are outside my home network unable to access server, as well as open for ISP to snoop into.
It's time to update the network here is what i came up.
here is what i came up.
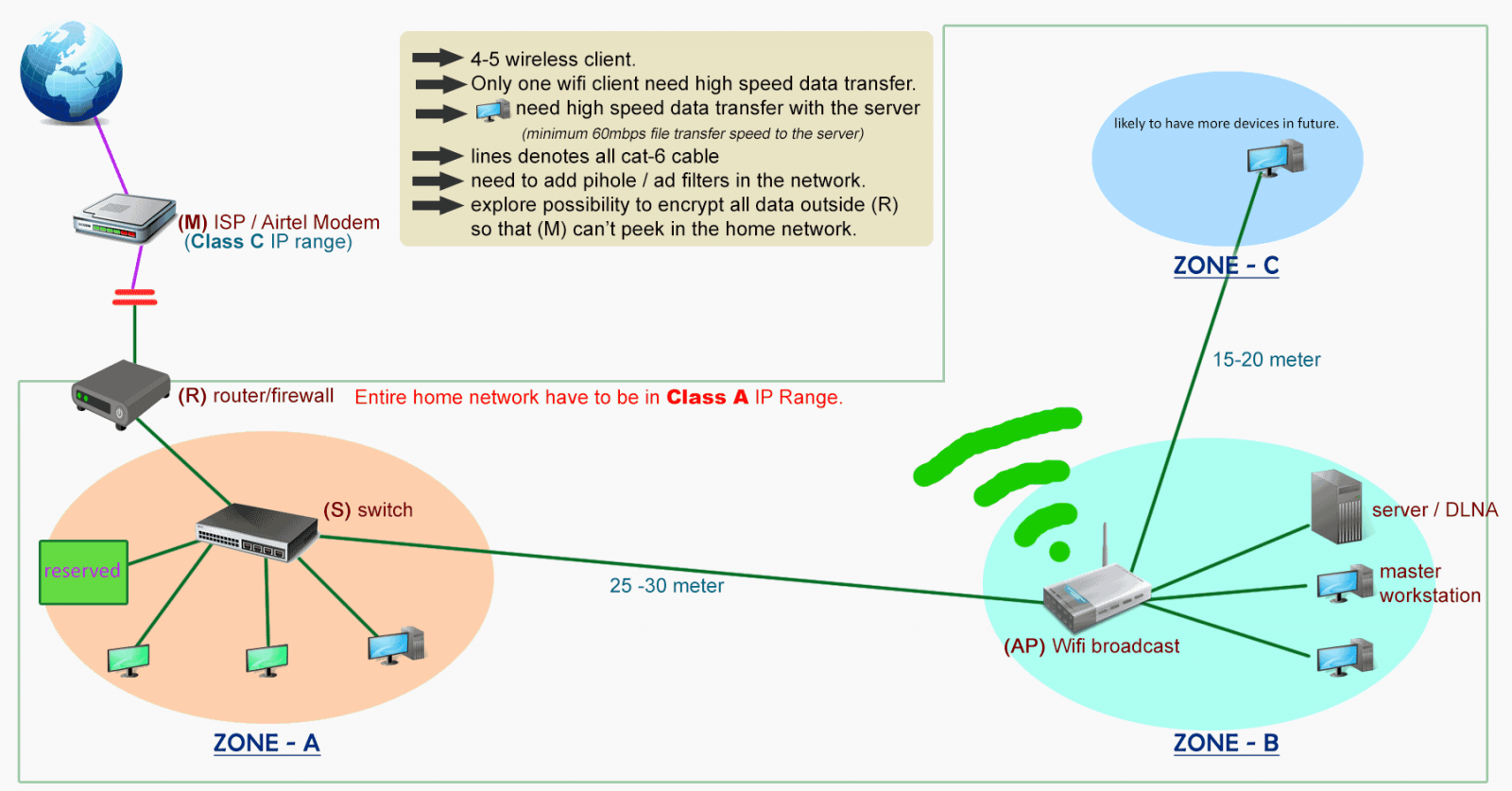
Power line already gone and replaced by cat6 to Zone-C (all future device in home will go in that zone ).
Please suggest if anyone finds a mistake or way to optimise it even more.
Not sure at which point i need to plug the pi-hole (coming soon).
Now looking for the main router ans network , which would help me isolate my home network from outer world.
Firewall/router (R)- I'm thinking to get this Ubiquiti USG (https://www.multilinkonline.com/Ubi...i-Security-Gateway-3xRJ45-Gigabit_p_1306.html)
I've seen in one review, that USG gateway don't provide us as much flexibility to configure and it over heats while heavy data transfers.
In that case what other option i do have ? -- (i would like to avoid configuration via CLI, i don't have that level of passion left at this point of life.)
other option ( will continue to list down, for my notes as well):
--> Linksys LRT224
Switch (S) - thinking about this https://www.multilinkonline.com/NET...witch-Desktop-101001000Mbps-GS205_p_1440.html , also was searching 10 GbE switch for future proofing, unable to find any. is it going to be overkill ?
Wireless network:
Will connect a Mi router, lying somewhere around in house directly to ISP router and make it open for guest and neighbours in wifi-n mode. Isolating totally form my home network. wil only keep in on when required.
Later (next year) i will replace the wifi router (AP) with a switch and attach a dedicated wifi AP ( something like UniFi nanoHD -https://store-ui.in/collections/unifi-network-wireless/products/unifi-nanohd-us ), separating wired and wireless networks. I will schedule it somehow to keep wifi during active only 10-12hrs a day.
Wifi point has to be in Zone -B for optimal coverage, going to have only 1 wireless device, n-mode for all mobile/tabs, and isolated ac-mode only for the wireless workstation which need high speed connection to home server. or probably something available which has dual non interfering AC broadcast. all the device in home can run ac network.
Pints to note:
1. Discourage consumer grade equipment and mostly looking for Uni/Cisco/netgear. (open to other stuffs which i'm not aware of but are budget friendly)
2. Don't want to spend a huge enthusiast level budget.
3. Will prefer devices with small form factor, which can disappear in the environment/hide in the cupboards.
4. Power consumption and heat produced - both should be minimal given they will be on 24x7x365.
List of important vidoes/link for future use (self-note):
1.
Security is the primary focus, looking for absolute control over the devices in network, should be able to define which client can access internet and what not.
Planing to build something which could last a decade.
my current setup looks something like:
With time, new clients added in network and few are outside my home network unable to access server, as well as open for ISP to snoop into.
It's time to update the network
Power line already gone and replaced by cat6 to Zone-C (all future device in home will go in that zone ).
Please suggest if anyone finds a mistake or way to optimise it even more.
Not sure at which point i need to plug the pi-hole (coming soon).
Now looking for the main router ans network , which would help me isolate my home network from outer world.
Firewall/router (R)- I'm thinking to get this Ubiquiti USG (https://www.multilinkonline.com/Ubi...i-Security-Gateway-3xRJ45-Gigabit_p_1306.html)
I've seen in one review, that USG gateway don't provide us as much flexibility to configure and it over heats while heavy data transfers.
In that case what other option i do have ? -- (i would like to avoid configuration via CLI, i don't have that level of passion left at this point of life.)
other option ( will continue to list down, for my notes as well):
--> Linksys LRT224
Switch (S) - thinking about this https://www.multilinkonline.com/NET...witch-Desktop-101001000Mbps-GS205_p_1440.html , also was searching 10 GbE switch for future proofing, unable to find any. is it going to be overkill ?
Wireless network:
Will connect a Mi router, lying somewhere around in house directly to ISP router and make it open for guest and neighbours in wifi-n mode. Isolating totally form my home network. wil only keep in on when required.
Later (next year) i will replace the wifi router (AP) with a switch and attach a dedicated wifi AP ( something like UniFi nanoHD -https://store-ui.in/collections/unifi-network-wireless/products/unifi-nanohd-us ), separating wired and wireless networks. I will schedule it somehow to keep wifi during active only 10-12hrs a day.
Wifi point has to be in Zone -B for optimal coverage, going to have only 1 wireless device, n-mode for all mobile/tabs, and isolated ac-mode only for the wireless workstation which need high speed connection to home server. or probably something available which has dual non interfering AC broadcast. all the device in home can run ac network.
Pints to note:
1. Discourage consumer grade equipment and mostly looking for Uni/Cisco/netgear. (open to other stuffs which i'm not aware of but are budget friendly)
2. Don't want to spend a huge enthusiast level budget.
3. Will prefer devices with small form factor, which can disappear in the environment/hide in the cupboards.
4. Power consumption and heat produced - both should be minimal given they will be on 24x7x365.
List of important vidoes/link for future use (self-note):
1.
Last edited: