Hi,
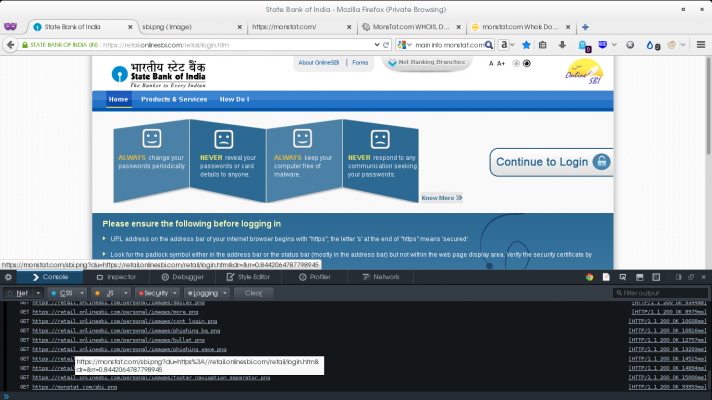
After about a week I opened SBI online banking page and saw little modified interface. I got alert.
Suddenly at the bottom of browser window I saw ''loading monstat.com...''
monstat.com?! I had never observed that thing ever hence I did't log in.
Then I opened the firefox dev tool and checked GET/POST data for this domain.
Its GETting:
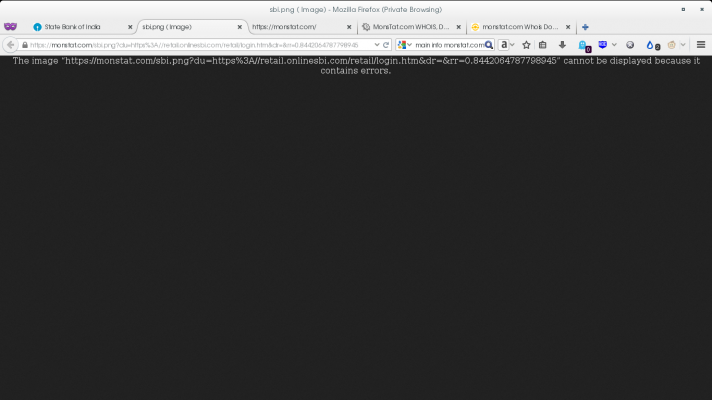
https://monstat.com/sbi.png?du=https://retail.onlinesbi.com/retail/login.htm&dr=&rr=0.5172883058151458
[rr] parameter value changes with each reload.
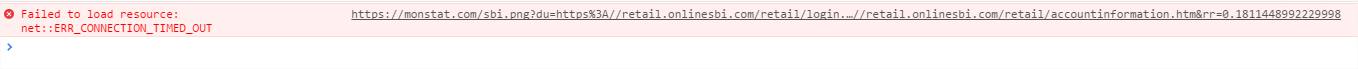
And monstat.com reponses with some invalid data (attachement: monstat.com response).
monstat.com itself responds with a blank page.
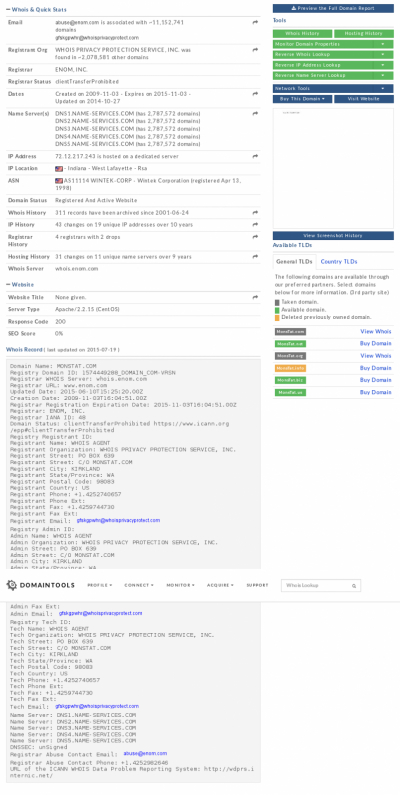
I checked domain info for monstat.com and found it more doubtful.
The monstat.com resource is not being directly called by html or javascript (I check the source of page, each js/css file).
Very probably some obfuscated js code is calling monstat.com.
I find it intrusive at a very wrong place and can compromise consumers security.
Even if SBI argues it could be for collecting user stats, for me its totally unacceptable.
They already collect a wealth of user stats (time/ip/activities/what not) after user logs in.
Are you also observing this thing loading when you open SBI netbanking login page?
Can it be anyway harmful?
I don;t think a bank can alllow such a shody thing on netbanking login page. Whats your view?
After about a week I opened SBI online banking page and saw little modified interface. I got alert.
Suddenly at the bottom of browser window I saw ''loading monstat.com...''
monstat.com?! I had never observed that thing ever hence I did't log in.
Then I opened the firefox dev tool and checked GET/POST data for this domain.
Its GETting:
https://monstat.com/sbi.png?du=https://retail.onlinesbi.com/retail/login.htm&dr=&rr=0.5172883058151458
[rr] parameter value changes with each reload.
And monstat.com reponses with some invalid data (attachement: monstat.com response).
monstat.com itself responds with a blank page.
I checked domain info for monstat.com and found it more doubtful.
The monstat.com resource is not being directly called by html or javascript (I check the source of page, each js/css file).
Very probably some obfuscated js code is calling monstat.com.
I find it intrusive at a very wrong place and can compromise consumers security.
Even if SBI argues it could be for collecting user stats, for me its totally unacceptable.
They already collect a wealth of user stats (time/ip/activities/what not) after user logs in.
Are you also observing this thing loading when you open SBI netbanking login page?
Can it be anyway harmful?
I don;t think a bank can alllow such a shody thing on netbanking login page. Whats your view?